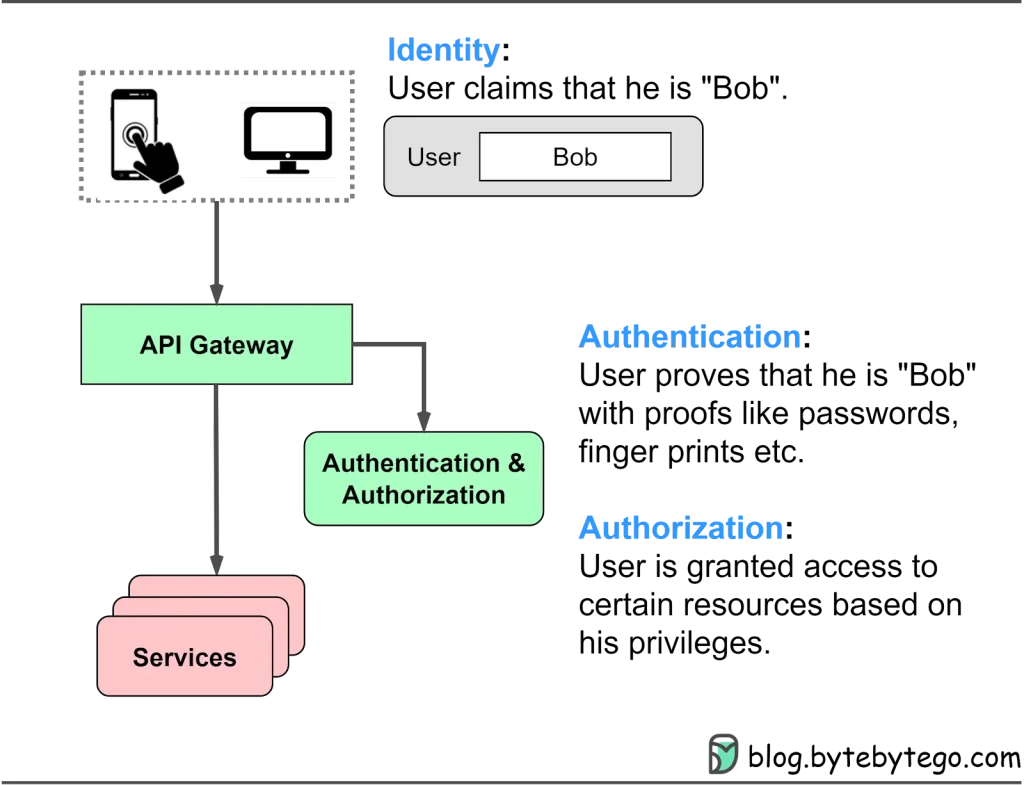
When utilizing a range of applications and websites, three fundamental security measures are consistently in action:
Identification: This refers to the process of establishing and confirming the user’s identity, ensuring that they are who they claim to be.
Authentication: Authentication is the method by which the system verifies the user’s identity. This step ensures that the user possesses the necessary credentials, such as a username and password, to access the system.
Authorization: Once a user has been authenticated, the system determines what actions and resources the user is permitted to access. Authorization defines the user’s level of access, which can range from read-only access to full administrative privileges.
The diagram below illustrates where these methods come into play within a typical website architecture and explains their significance.
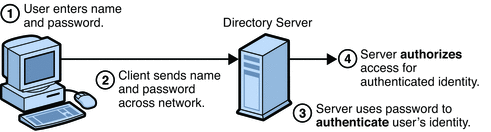
Throughout this two-part series, we explore various authentication techniques, covering topics such as passwords, sessions, cookies, tokens, JWTs (JSON Web Tokens), SSO (Single Sign-On), and OAuth2. We delve into the specific challenges that each of these methods addresses and provide guidance on selecting the most suitable authentication approach to meet our specific requirements.
Password Authentication
Password authentication stands as a foundational and extensively employed method for confirming a user’s identity across websites and applications. In this approach, users input their distinct username and password pair, serving as their digital keys to unlock access to secured resources. The system then verifies these supplied credentials against the stored user data, and if there’s a match, it grants the user permission to enter.
Although password authentication is a bedrock method for user validation, it bears certain limitations. Passwords can be forgotten, and managing a multitude of unique username-password pairs for various online platforms can pose a considerable challenge. Furthermore, password-centric systems are susceptible to security threats, including brute-force and dictionary attacks, in the absence of robust security safeguards.
To tackle these challenges, contemporary systems frequently integrate added layers of security, like multi-factor authentication, or opt for alternative authentication mechanisms, such as session-cookie or token-based authentication. These measures either enhance or replace password-based authentication for subsequent access to safeguarded resources.
In this section, we will begin our exploration with password-based authentication, delving into its historical roots and operational principles.
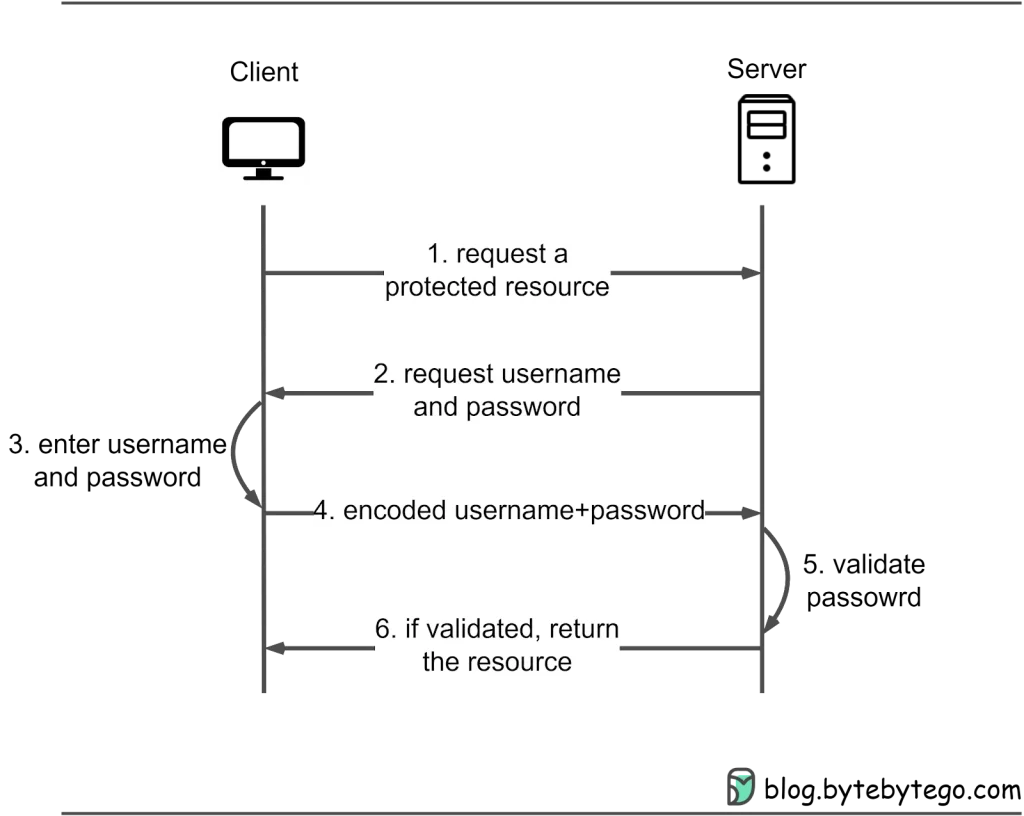
HTTP Basic Access Authentication
HTTP basic access authentication necessitates a web browser to furnish both a username and a password when seeking access to a safeguarded resource. These credentials are encoded using the Base64 algorithm and are appended to the HTTP header field called Authorization, tagged as ‘Basic.’
Here’s a typical sequence of events:
1.The client initiates a request to gain entry to a secured resource on the server.
2.If the client hasn’t yet provided any authentication credentials, the server responds with a 401 Unauthorized status code and includes the WWW-Authenticate: Basic header, signaling the need for basic authentication.
3.The client, in turn, prompts the user to input their username and password, which are then amalgamated into a single string, structured as username:password.
4.This merged string undergoes Base64 encoding and gets embedded in the “Authorization: Basic” header for the subsequent request to the server, resulting in a format like Authorization: Basic dXNlcm5hbWU6cGFzc3dvcmQ=.
5.Upon receiving this request, the server deciphers the Base64-encoded credentials, discerns the username and password, and then crosschecks these with its own user database or authentication service.
6.Should the credentials validate successfully, the server grants access to the requested resource. In cases where there’s no match, the server responds with a 401 Unauthorized status code.
HTTP Basic Access Authentication does come with its share of shortcomings. The encoded username and password using Base64 can be relatively easily decoded. In an effort to enhance security, most websites adopt TLS (Transport Layer Security) for data encryption between the browser and server. However, even with TLS, users’ credentials can still be exposed to interception or man-in-the-middle attacks.
With HTTP Basic Access Authentication, the browser consistently sends the Authorization header with the requisite credentials for each request to secured resources within the same domain. This contributes to a more seamless user experience, eliminating the need for recurrent username and password entries. Yet, since each website manages its own set of usernames and passwords, users may grapple with memorizing their multiple sets of credentials.
As of today, this authentication mechanism is deemed outdated for contemporary websites and their security requirements.
Session-Cookie Authentication
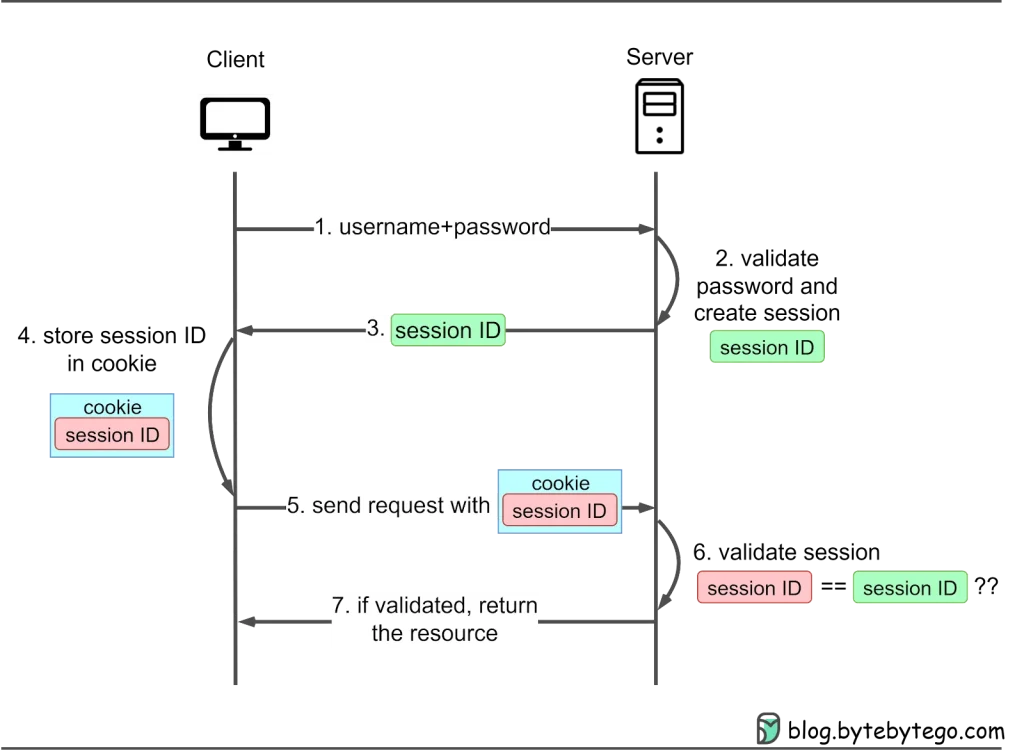
Session-cookie authentication serves as a solution to the limitations of HTTP basic access authentication when it comes to monitoring a user’s login status. It hinges on the generation of a session ID to track a user’s status during their visit. This session ID is maintained both on the server-side and within the client’s cookie, functioning as a means of authentication. It’s aptly named a session-cookie because it essentially represents a cookie housing the session ID.
Here’s an overview of how it operates:
The client initiates a request to access a secure resource on the server. In cases where the client hasn’t yet authenticated, the server responds with a login prompt. The client subsequently supplies their username and password.
The server proceeds to verify the provided credentials by cross-referencing them with its user database or authentication service. Upon a successful match, the server generates a unique session ID and creates a corresponding session within the server-side storage, which can take the form of server memory, a database, or a session server.
The server dispatches the session ID to the client as a cookie, usually accompanied by a Set-Cookie header.
The client retains and stores this session cookie.
For any subsequent requests, the client dispatches this cookie within the request headers.
The server, in turn, validates the session ID within the cookie by comparing it against the stored session data, thereby authenticating the user.
Upon successful validation, the server permits access to the requested resource. In the event the user logs out or after a predetermined duration of inactivity, the server invalidates the session, and the client discards the session cookie.
A Comparison
Let’s compare these authentication mechanisms to better understand their use cases and limitations:
Passwords: Simple and widely used, but vulnerable to various attacks and often require additional security measures like MFA.
Session Management and Cookies: Useful for maintaining user state within a single application but have limitations when it comes to cross-application authentication.
Tokens and JWTs: Versatile and secure, especially for APIs and cross-application authentication.
Single Sign-On (SSO): Ideal for simplifying access across multiple applications, streamlining user management, and improving user experience.
OAuth: Essential for authorizing third-party applications and protecting user data when interacting with external services.
Best Practices for Modern Authentication
To ensure robust and secure authentication in today’s digital landscape, consider the following best practices:
Implement Strong Password Policies: Encourage users to create complex passwords and consider MFA for added security.
Secure Session Management: Use secure cookies and guard against common session vulnerabilities like session fixation and session hijacking.
Adopt Token-Based Authentication: Use tokens or JWTs for authentication and authorization in your applications.
Leverage Single Sign-On (SSO): If your organization uses multiple applications, consider implementing SSO to simplify user access.
Embrace OAuth: If your application interacts with third-party services, OAuth is a secure way to authorize access.
Regularly Update and Audit: Continuously review and update your authentication mechanisms and practices to stay ahead of evolving threats.

The Future of Authentication
As technology advances, the field of authentication continues to evolve. Biometric authentication, passwordless logins, and blockchain-based identity verification are just a few examples of where authentication may be headed in the future. These innovations aim to enhance security and user convenience while minimizing the vulnerabilities associated with traditional passwords.
Conclusion
Authentication is the cornerstone of our online security, and understanding the various mechanisms is vital for developers, businesses, and end-users alike. From the conventional password to cutting-edge technologies like JWTs, SSO, and OAuth, the world of authentication offers a diverse toolkit to cater to different needs and levels of security. By adopting best practices and staying informed about emerging technologies, we can ensure that our digital identities remain safe and secure in an ever-changing online landscape.
Get a New Way to See the World. Connect with us today and let us know how we can help you. Read more innovative stuff here.
For any questions, suggestions, feedback, or comments, please E-mail us. [email protected]
Thank You!
Follow and clap for more industry trends and news.